Cyber attacks are predicted to cost the global economy $9.5 trillion this year.1 As a result, both network operations center (NOC) and security operations center (SOC) teams are essential for protecting businesses in today's threat landscape.
However, the lines between network operations and security operations have blurred in recent years. While both play critical roles in safeguarding an organization's IT systems, they have different responsibilities and skill sets. Many businesses treat NOC and SOC as interchangeable or keep them siloed in separate departments, creating confusion about the responsibilities of each department.
Understanding the differences between NOC and SOC can help your business leverage these teams more effectively – and strengthen your network's security and performance. Read on to explore the responsibilities of each, their differences, and how they work together to protect your network.
What Is A Network Operations Center?
A network operations center (NOC) is a centralized location where IT engineers and technicians monitor and manage an organization's network infrastructure. The NOC team minimizes downtime and ensures optimal network performance.
NOC teams help companies meet service level agreements (SLAs) for customers by addressing network performance and availability issues. They watch for technical issues like server outages, slow internet speeds, or network congestion and troubleshoot problems. They also schedule updates and patches to ensure consistent performance and reliability.
NOCs play a critical role in incident response by identifying problems and containing issues before they can cause business disruptions. Essentially, they provide the backbone to keep systems running smoothly.
What Is A Security Operations Center?
A security operations center (SOC) serves as a central hub for protecting an organization from cyber threats. SOC teams are responsible for detecting, analyzing, and responding to any security incidents that could impact the IT network and result in system failures.
SOC analysts apply specialized tools and techniques to monitor networks for suspicious activity, such as security breaches, malware infections, and other cyber attacks. As security professionals, they investigate alerts, determine if they are real threats, and respond quickly to mitigate damages.
In addition to monitoring networks, SOCs also analyze security trends to identify vulnerabilities and proactively address risks. SOCs are on the frontlines of defending organizations against future attacks and data loss.

What Challenges Do Security Operations Centers Face?
With the number of security threats increasing, SOCs face some unique challenges. Some of the most pressing issues modern security operations center staff face today include:
- Alert Fatigue - SOCs can be flooded with a high volume of alerts from various security tools – 59% of security professionals receive over 500 alerts daily, and 38% receive more than 1,000 daily.2 Alert fatigue makes triaging and prioritizing threats difficult.
- Data Integration - Many data sources across enterprise businesses are siloed, and connecting the dots can be manual and time-intensive.
- Too Many Tools - Analysts often juggle an overwhelming number of security technologies from various vendors.
- Talent Shortages - The global cyber security skills gap makes hiring and retaining skilled SOC analysts challenging. Over half (54%) of cyber security professionals say the impact of the talent shortage has worsened over the past two years.3
- Lack of Automation - Without automation tools, tedious tasks like reporting still require manual efforts and slow response times.
NOC vs SOC - What Are The Differences?
Both NOC and SOC are essential for maintaining a company's IT infrastructure, but they serve distinct roles.
- While a NOC ensures the overall performance and uptime of a network, a SOC focuses on identifying and mitigating security threats.
- NOCs are staffed with network engineers who specialize in troubleshooting and maintaining network health, while SOCs are managed by cybersecurity experts trained to detect and respond to cyber threats.
- The tools used also differ—NOCs rely on network performance monitoring tools, whereas SOCs utilize advanced security solutions to detect and prevent breaches.
Understanding these differences is key to ensuring both operational efficiency and robust security for an organization.
So, let's explore NOC vs SOC differences in more detail.
While NOCs and SOCs both monitor networks, they focus on different areas:
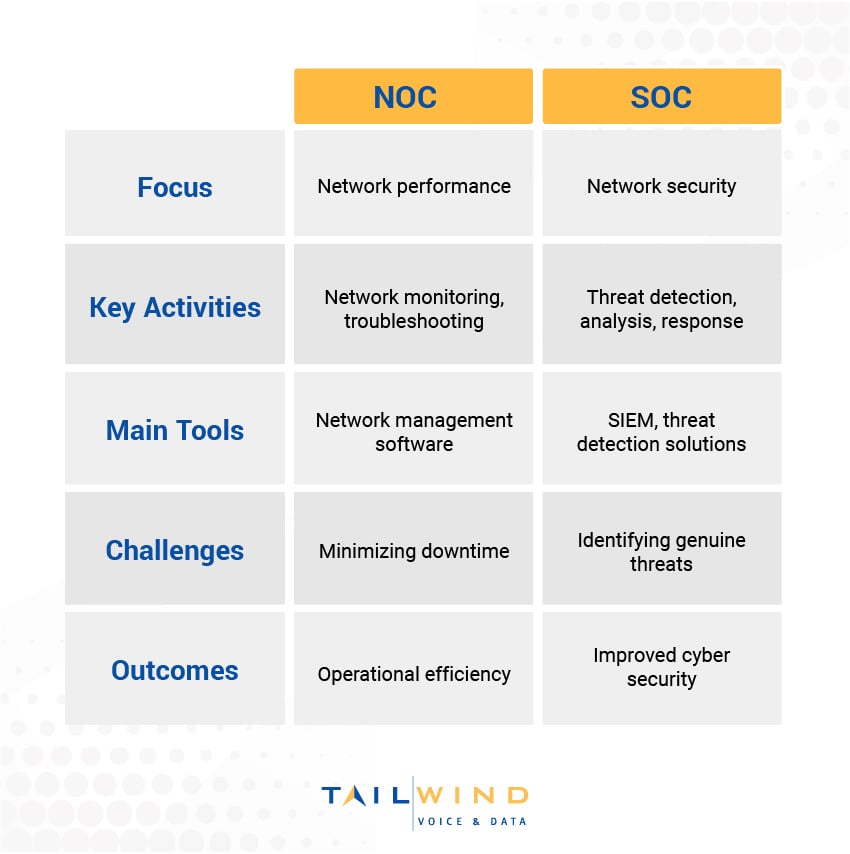
NOC vs SOC Focus
The NOC's focus is on maintaining and optimizing network infrastructure. Their objective is to ensure IT systems run smoothly and minimize downtime that could impact normal operations.
SOC analysts are dedicated to protecting the network and corporate IT assets from security incidents and cyber threats. Their goal is to prevent future attacks and data breaches that could lead to service disruptions, financial losses, or reputational damage.
Key Activities
NOC staff are responsible for monitoring network infrastructure health, quickly troubleshooting any performance issues, implementing business continuity measures to protect against natural disasters, and proactively addressing capacity planning.
SOC teams monitor systems for suspicious activity or security events, investigate alerts to determine if they are real threats to the network, and orchestrate responses to confirmed incidents.
Main Tools
NOC analysts rely on network management and monitoring tools to maintain visibility and control across the corporate infrastructure.
SOCs leverage security information and event management (SIEM) platforms as well as specialized threat detection solutions to identify risks.
Challenges
NOC teams aim to minimize network downtime events, as even brief service outages can impact revenue and customer satisfaction.
SOC challenges typically include accurately identifying genuine security threats amongst the many alerts and false positives generated by various security solutions.
Outcomes
By ensuring optimal network performance, NOC analysts enable operational efficiency across the business and provide excellent customer experiences.
Effective threat detection and rapid response by the SOC team results in improved cyber security defenses and reduced risk of damaging data breaches.
Which Is Better For Your Business?
Determining whether to invest more in NOC or SOC capabilities depends on your business needs and security risks. Here are a few factors to consider:
- How critical is uptime versus breach prevention? Downtime losses or data leakage costs?
- What's the current maturity level of your NOC and SOC teams?
- Does your business network face higher infrastructure risks or cyber threats?
- What are your compliance requirements driving security investments?
- Can your existing teams handle the workload, or is outsourcing needed?
For most organizations, having strong NOC and SOC capabilities goes hand in hand. The NOC is responsible for ensuring your network infrastructure can maintain business operations, while the SOC protects your business from cyber threats that could result in network and business disruptions.
Solve Your Enterprise Network Problems With Tailwind NOCaaS
Both NOC and SOC teams play integral roles in maintaining and securing your corporate network. Unfortunately, the high costs of maintaining an on-site network operations center and ensuring specialized staff are trained properly can be difficult to justify. Outsourcing these services to a reliable NOC provider ensures your business has the right people and processes to support employees and customers around the clock.
For enterprise businesses looking to eliminate the headache of managing network operations without losing control, TailWind provides a complete NOC as a service (NOCaaS) solution. Trust our experts to deliver:
- Local and Accountable Support - We provide on-site assistance from field techs across North America who operate as an extension of your team.
- Scalable Infrastructure Management - We'll get to know your operations, so we’re always ready to address your unique needs with the correct resources.
- End-to-End Solutions - We own your tickets from start to finish, providing true end-to-end network management with real-time tracking.
- Reduced Costs and Risks - We'll leverage our experience, practices, and toolsets to reduce your high fixed NOC costs and eliminate downtime risks.
Ready to get started with NOCaaS services tailored to meet the needs of your multi-location enterprise? Reach out to TailWind today.
Sources:


